I was having this issue after I submitted a job. This was due to some configuration I had to do to improve security which is similar to Using the Host’s FirewallD as the Main Firewall to Secure Docker
qsub: Budget Manager: License is unverified. AM is not handling requests
To resolve the issue, I took the following Steps. On the PBS-Control Server,
Step 1: Export the Path of the AM Database.
export PATH=/opt/am/postgres/bin:$PATHStep 2: Check that the Docker Container Services are started in the System. You may want to start the dockers to capture any errors. If the docker is not able to start up, it is likely due to the firewall settings.
# systemctl status firewalld.service.Step 3: I restarted the PBS Altair Service
# systemctl restart altaircontrol.serviceStep 4: I use the Docker Command to return an overview of all running containers
# docker ps 
At the PBS-Server, Restart the AM Control Register is working
# /opt/am/libexec/am_control_register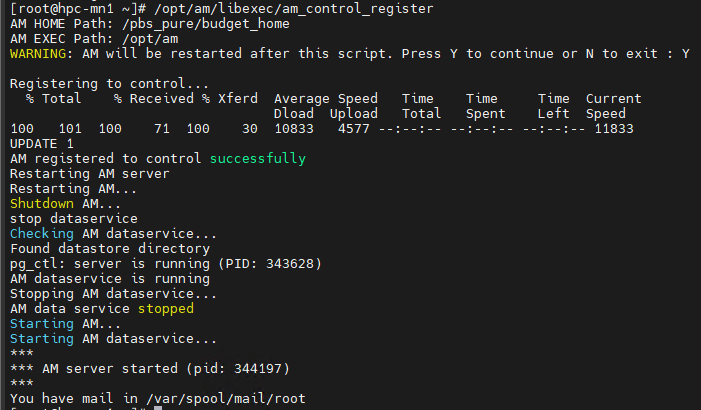
To Test, Submit an Interactive Job with the correct Project Code, it should work.
