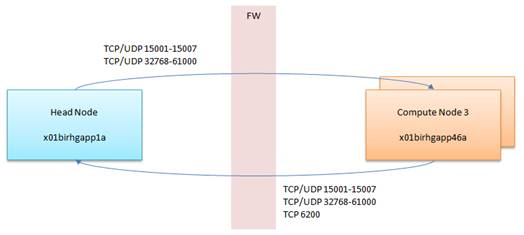
Note: Do note that the default zone is “public”
Section 1: Checking Zones and Prerequisites
Option 1: Check State of Firewalld
# firewall-cmd --state
Running
Option 2: Check Default Zone
# firewall-cmd --get-default-zone
public
Option 3: Check Active Zones
# firewall-cmd --get-active-zones
public: etho eth1
Option 4: Get Zones
# firewall-cmd --get-zones
block dmz drop external home internal public trusted work
Section 2: Selecting Zones for your Interfaces
Option 1: Change Interfaces
# firewall-cmd --permanent --zone=trusted --change-interface=eth0
success
# firewall-cmd --reload
Option 2: Verify the Zone has been changed
firewall-cmd --get-active-zones
trusted
interfaces: eth0
public
interfaces: eth1
Section 3: Editing Firewall-CMD Rules
Option 1: Opening Ports (Single)
# firewall-cmd --permanent --zone=public --add-port=80/tcp
success
# firewall-cmd --reload
Option 2: Opening Ports (Range)
# firewall-cmd --permanent --zone=public --add-port=80-90/tcp
success
# firewall-cmd --reload
Option 3: List Ports
# firewall-cmd --zone=public --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: enp6s0f0 eno2 ib1
sources:
services: ssh dhcpv6-client
ports: 22/tcp 5053/tcp 57889/tcp
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
Option 4: Remove Port
# firewall-cmd --permanent --zone=public --remove-port=80/tcp
success
# firewall-cmd --reload
Option 5: Adding Service
Checking Services
# firewall-cmd --get-services
Finally, add service – ssh
# firewall-cmd --permanent --zone=public --add-service=ssh
success
# firewall-cmd --reload
Source-Based Filtering with zones and IP Addresses
Add the Source IP Addresses to the Zone (Assume you are limiting IP Addresses on the trusted zone)
firewall-cmd --zone=trusted --add-source=192.168.1.0/24 --permanent
success
firewall-cmd --reload
Make sure the Ethernet is in the trusted zone. To move the ethernet into the trusted zone, see Section2 in the same blog
If you are outside the allowed IP Address, you should see something like (Assume your trusted target server is 192.168.1.1 and your external untrusted client is 192.168.2.0), you might see something like this
ssh user1@192.168.1.1
Password:
Internal errors
References:
- How To Set Up a Firewall Using FirewallD on CentOS 7