Taken from [TIPS] A Centrify Server Suite Cheat Sheet
BASIC Troubleshooting
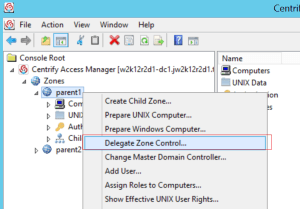
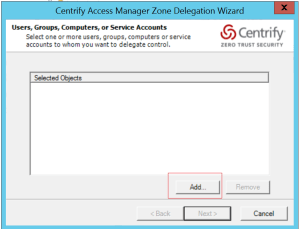
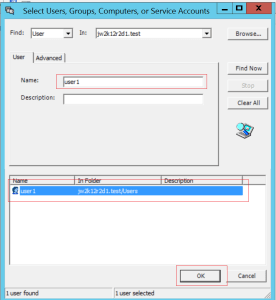
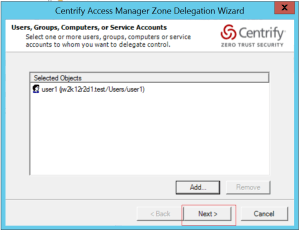
Pt 1. To check the general status of the client
$ adinfoLocal host name: xxx
Joined to domain: xxx.com
Joined as: xxx
Pre-win2K name: xxx
Current DC: xxx
Preferred site: NTU-Site
Zone: xxx
Last password set: 2019-07-24 06:29:08 +08
CentrifyDC mode: connected
Licensed Features: EnabledPt 2. To see the corresponding Centrify Suite Version
$ adinfo --suite-versionadinfo (CentrifyDC 5.5.0-200) Centrify Server Suite 2018
Pt 3. To view Active Directory connectivity to the current domain
$ adinfo --testDomain Diagnostics:
Domain:
DNS query for:
DNS query for:
Testing Active Directory connectivity:
Domain Controller:
ldap: 389/tcp - good
ldap: 389/udp - good
smb: 445/tcp - good
kdc: 88/tcp - good
kpasswd: 464/tcp - good
ntp: 123/udp - good
Domain Controller:
ldap: 389/tcp - good
ldap: 389/udp - good
smb: 445/tcp - good
kdc: 88/tcp - good
kpasswd: 464/tcp - good
ntp: 123/udp - good
Domain Controller:
ldap: 389/tcp - good
ldap: 389/udp - good
smb: 445/tcp - good
kdc: 88/tcp - good
kpasswd: 464/tcp - good
ntp: 123/udp - good
Domain Controller:
ldap: 389/tcp - good
ldap: 389/udp - good
smb: 445/tcp - good
kdc: 88/tcp - good
kpasswd: 464/tcp - good
ntp: 123/udp - goodPt 4: To see the current joined Centrify zone
$ adinfo --zonexxx.com/MyOU/Centrify/Zones/GlobalADVANCED / TROUBLESHOOTING Information
Pt 5: To check the status of the DNS cache and stats
$ adinfo --diag dns
adinfo (CentrifyDC 5.5.0-200)Host Diagnostics
uname: Linux hpc-gekko1 3.10.0-693.el7.x86_64 #1 SMP Tue Aug 22 21:09:27 UTC 2017 x86_64
OS: CentOS
Version: 7.0
Number of CPUs: 32
…..
…..Pt 6: To check network connectivity statistics
$ adinfo --sysinfo netstateSystem Diagnostic
===============Network State===================
Site Map
com.sg=>PreferredSite:XXX.com, SubnetSite:XXX-Site
Domain Map
…
…
state: alive
swept: 21 mins ago
...Pt 7: To see the status of the AD computer trust relationship
$ adinfo --sysinfo adagentSystem Diagnostic
===================adagent internals===================
Binding Table
$=>main11.main.ntu.edu.sg(MAIN.NTU.EDU.SG) connected
xxx.com=>xxx.com disconnected
xxx1=>xxx1.com disconnected
xxx2=>xxx2.com connected
xxx3=>xxx3.com connectedTESTING Credentials Information
$ adinfo -A --user myuseridActive Directory password:
...