Muco of the Troubleshooting comes from the Knowledgebase Article is derived from KB-8958: MFA with DirectControl fails with SSL connection error and Preparing a Linux Client Server for Centrify and 2FA for CentOS-7
Problem :
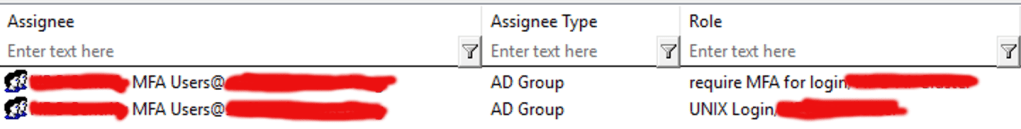
When attempting to log in with a user that requires MFA the following error is presented:
$ ssh user@192.168.0.1
SSL Connection ErrorCause:
The error is likely due to a certificate problem. A required certificate may be missing or the permission may not be set correctly
How to check:
# /usr/share/centrifydc/bin/adcdiagVERSION : Verify that DirectControl version supports MFA : Pass
JOINSTATE : Verify that DirectControl is in connected mode : Pass
ZONECHK : Verify that MFA is supported in the zone : Pass
SSHDCFG : Verify that SSHD enables ChallengeResponseAuthentication : Warning
: Cannot read sshd configuration file. Probably you are not
: using Delinea openssh. SSH login for MFA users will fail if
: option ChallengeResponseAuthentication is not set to yes.
: Please check and ensure ChallengeResponseAuthentication is
: set to yes in sshd configuration file.
CDCCFG : Verify that MFA options in centrifydc.conf are correct : Pass
PROXYCFG : Verify that HTTP proxy configuration is set properly : Pass
CLDINST : Verify that trusted Identity Platform instance is specified : Pass
: Successfully connected to Identity Platform and certificate
: has been verified OK.
CNTRCFG : Verify that Connectors are configured correctly : Pass
CURCNTR : Verify that DirectControl has selected a workable Connector : Pass
CLOUDROLE : Verify that this machine has permissions to perform Identity
: Platform authentication : Pass
......
......
......Check the Logs at /var/centrify/tmp…. You may notice some errors like
.....
.....
ERROR:
Not a trusted connector or no valid connector certificate installed locally.
SUGGESTIONS:
1. Verify that the IWA root CA certificate is installed in the system. Please refer to KB-7393 on how to configure the root CA certificate in the system.
2. Please collect connector log if you need Delinea support.
.....
.....Resolution:
Check whether the Certificates have been added at
- /etc/pki/ca-trust/source/anchors/
- /var/centrify/net/certs
Check the SSH Settings at
# vim /etc/ssh/sshd_config# To disable tunneled clear text passwords, change to no here!
#PasswordAuthentication yes
#PermitEmptyPasswords no
PasswordAuthentication no
# Change to no to disable s/key passwords
#ChallengeResponseAuthentication yes
ChallengeResponseAuthentication yesRestart the SSHD Services
# systemctl restart sshd.serviceRestart the Centrifydc services
# /usr/share/centrifydc/bin/centrifydc restartActive Directory Flush and Reload
# adflush -f
# adreload